November 11, 2025
SEOUL – North Korean state-sponsored hackers hijacked Google accounts to remotely control and wipe smartphones and tablets held by individuals in South Korea, then exploited their KakaoTalk messenger as a channel to spread malware to their contacts, a report said Monday.
The attack marks the first confirmed case of a North Korean state-sponsored hacking group compromising Google accounts to gain remote control over smart devices, according to South Korean cybersecurity firm Genians.
The attack was identified as part of a malware campaign by North Korea’s KONNI APT cyber espionage group.
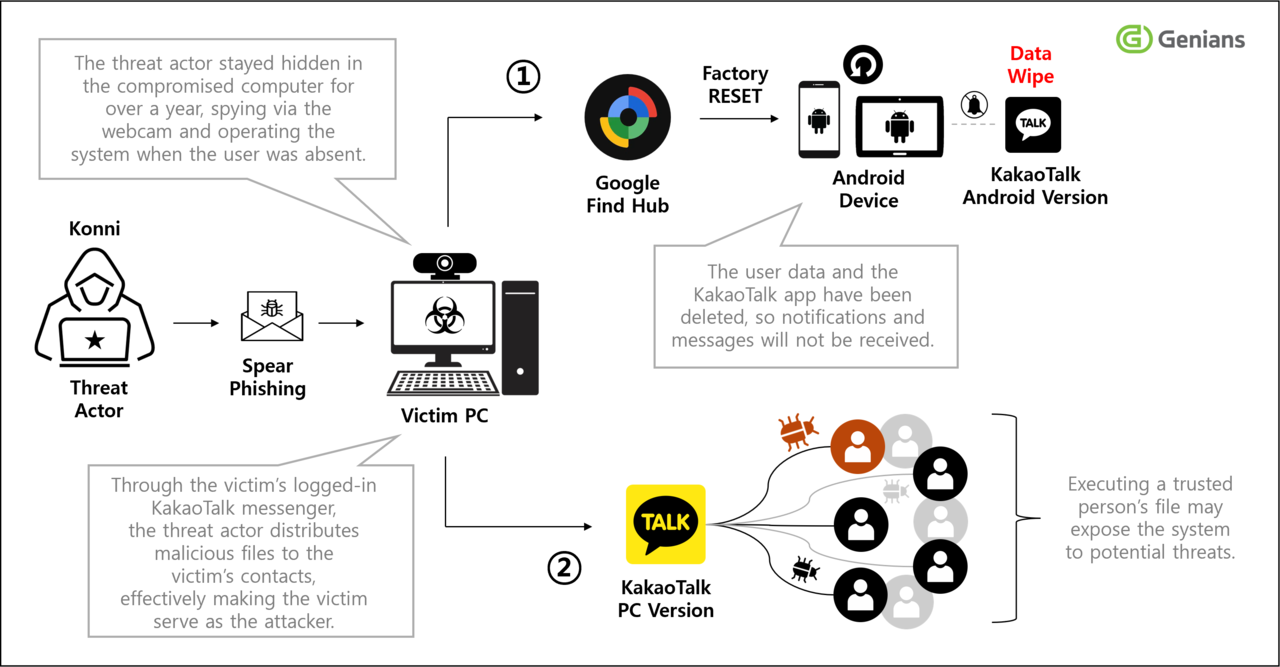
Attack flowchart provided by Genians
In the first stage of the hacking scenario, hackers infiltrated targeted individuals’ devices through spear-phishing attacks by impersonating South Korea’s tax agency, the National Tax Service.
Then, hackers conducted extensive internal reconnaissance and user information gathering before launching the cyberattack.
Next, hackers compromised victims’ Google accounts and exploited the Google “Find Hub” service, originally intended by Google to protect lost or stolen Android devices, for data-destructive attacks.
However, hackers abused key functions of the Find Hub service, which allows users to execute a variety of remote commands on registered Android-based devices, to perform location tracking and remotely reset smartphones and tablets.
“This development demonstrates a realistic risk that the feature can be abused within APT campaigns,” the English-language report read.
More seriously, the North Korean cyberattackers compromised victims’ KakaoTalk accounts, utilizing them as primary channels to spread malicious files to their contacts.
The compromising of KakaoTalk accounts was carried out after resetting the victims’ Android devices, disrupting and delaying the normal recovery and use of the targeted smart devices for an extended period.
Specifically, the hackers executed a remote factory-reset command on victims’ Android devices after confirming via Find Hub’s location query that the victims were not using their devices.
The remote reset halted normal device operation, blocked notifications and message alerts from the KakaoTalk messaging app, and effectively prevented victims from seeing alerts and delaying detection and response.
Immediately after the reset, the attacker used the victim’s logged-in KakaoTalk PC version as a second distribution channel to rapidly spread malicious files.
“This campaign is assessed as a typical social-engineering attack that leveraged trust-based communications to precisely exploit the target’s psychological and social context,” according to the report.
“In particular, the compromise of messenger accounts and their use as a secondary attack vector increased the attack’s level of customization while expanding its attack surface and propagation scope, thereby amplifying the threat.”

The image provided by Genians shows North Korean hackers sending a malicious file disguised as a “stress-relief program” to North Korean defector students after compromising the KakaoTalk messenger account of a specialist counselor.
The report found that victims included a specialist counselor who provides psychological support to North Korean defector students.
Hackers took over and used the KakaoTalk account of the counselor on Sept. 5 to send a malicious file disguised as a “stress-relief program” to North Korean defector students. When recipients opened the file, it infected their devices.
On Sept. 15, a separate similar incident occurred in which malicious files were widely and simultaneously distributed via another victim’s KakaoTalk account.
“This combination of device neutralization and account-based propagation is unprecedented among previously known state-sponsored APT scenarios and was first identified and analyzed in this report,” the company said. “It demonstrates the attacker’s tactical maturity and advanced evasion strategy, marking a key inflection point in the evolution of APT tactics.”


